Which Of The Following Are Secure Network Protocols Select Two 70+ Pages Summary [1.5mb] - Latest Update
95+ pages which of the following are secure network protocols select two 2.3mb. Of the three existing versions of the Simple Network Management Protocol SNMP versions 1 and 2 SNMPv1 and SNMPv2 offer authentication based on community strings sent in an unencrypted form in cleartext. SSL A technician has been tasked with changing the settings for a used SOHO router but does not have the administrator password because the previous owner changed it. Prioritize Those With Highest Impact First - Learn More. Read also following and understand more manual guide in which of the following are secure network protocols select two Which of the following are secure network protocols.
Both A and C. HTTP is used for transferring data between the client browser request and the web server response in the hypertext format same in case of HTTPS except that the transferring of data.

7 Osi Layers Of Munications In 2021 Osi Layer Munication Munication Works
| Title: 7 Osi Layers Of Munications In 2021 Osi Layer Munication Munication Works |
| Format: PDF |
| Number of Pages: 304 pages Which Of The Following Are Secure Network Protocols Select Two |
| Publication Date: August 2017 |
| File Size: 2.8mb |
| Read 7 Osi Layers Of Munications In 2021 Osi Layer Munication Munication Works |
 |
Networking Show Answer Hide Answer Correct Answer.

SSL and TLS HTTPS. Common applications include remote command-line login remote command execution but any network service can be secured with SSH. Its predecessor Secure Sockets Layer SSL which is now prohibited from use - are cryptographic protocols that provide communications security over a computer network. However TLS is a successor version of SSL. Answered Dec 28 2016 by Giordano_TX. Such protocols ensure the data delivery in a secure way between two ends.

Work Enterprise Diagram Working Basics Cisco Working Technology Puter Work
| Title: Work Enterprise Diagram Working Basics Cisco Working Technology Puter Work |
| Format: ePub Book |
| Number of Pages: 149 pages Which Of The Following Are Secure Network Protocols Select Two |
| Publication Date: September 2018 |
| File Size: 6mb |
| Read Work Enterprise Diagram Working Basics Cisco Working Technology Puter Work |
 |
14 Most Mon Work Protocols And Their Vulnerabilities Geeksfeeks
| Title: 14 Most Mon Work Protocols And Their Vulnerabilities Geeksfeeks |
| Format: ePub Book |
| Number of Pages: 130 pages Which Of The Following Are Secure Network Protocols Select Two |
| Publication Date: August 2021 |
| File Size: 1.5mb |
| Read 14 Most Mon Work Protocols And Their Vulnerabilities Geeksfeeks |
 |

Puter Working Puter Science Programming Working Infographic Puter Learning
| Title: Puter Working Puter Science Programming Working Infographic Puter Learning |
| Format: eBook |
| Number of Pages: 254 pages Which Of The Following Are Secure Network Protocols Select Two |
| Publication Date: March 2020 |
| File Size: 6mb |
| Read Puter Working Puter Science Programming Working Infographic Puter Learning |
 |

What Is Ssh Secure Shell Or Ssh Ssh Terminal Server Is A Work Protocol That Allows Data Exchange Through A Secure Cha Accounting Secure Shell Working
| Title: What Is Ssh Secure Shell Or Ssh Ssh Terminal Server Is A Work Protocol That Allows Data Exchange Through A Secure Cha Accounting Secure Shell Working |
| Format: eBook |
| Number of Pages: 136 pages Which Of The Following Are Secure Network Protocols Select Two |
| Publication Date: February 2017 |
| File Size: 2.3mb |
| Read What Is Ssh Secure Shell Or Ssh Ssh Terminal Server Is A Work Protocol That Allows Data Exchange Through A Secure Cha Accounting Secure Shell Working |
 |
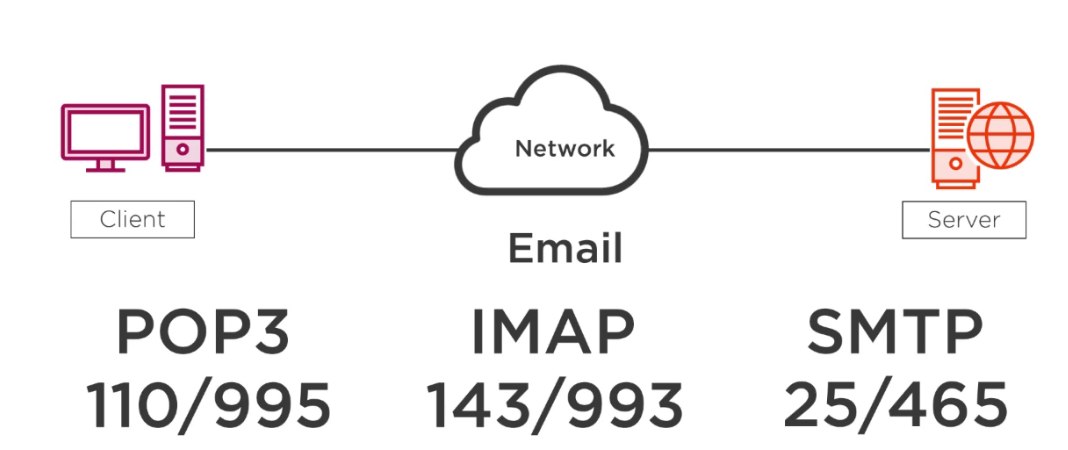
Types Of Working Protocols Top Four Major Protocols Of Working
| Title: Types Of Working Protocols Top Four Major Protocols Of Working |
| Format: ePub Book |
| Number of Pages: 303 pages Which Of The Following Are Secure Network Protocols Select Two |
| Publication Date: November 2019 |
| File Size: 1.7mb |
| Read Types Of Working Protocols Top Four Major Protocols Of Working |
 |

Yersinia Is A Framework For Performing Layer 2 Attacks The Following Protocols Have Been Implemented In Yersinia Puter Security Hacking Puter Tech Hacks
| Title: Yersinia Is A Framework For Performing Layer 2 Attacks The Following Protocols Have Been Implemented In Yersinia Puter Security Hacking Puter Tech Hacks |
| Format: ePub Book |
| Number of Pages: 262 pages Which Of The Following Are Secure Network Protocols Select Two |
| Publication Date: September 2019 |
| File Size: 725kb |
| Read Yersinia Is A Framework For Performing Layer 2 Attacks The Following Protocols Have Been Implemented In Yersinia Puter Security Hacking Puter Tech Hacks |
 |
Types Of Working Protocols Top Four Major Protocols Of Working
| Title: Types Of Working Protocols Top Four Major Protocols Of Working |
| Format: eBook |
| Number of Pages: 306 pages Which Of The Following Are Secure Network Protocols Select Two |
| Publication Date: January 2020 |
| File Size: 1.3mb |
| Read Types Of Working Protocols Top Four Major Protocols Of Working |
 |

Tcp Ip Protocols Working Basics Puter Work Puter Technology
| Title: Tcp Ip Protocols Working Basics Puter Work Puter Technology |
| Format: ePub Book |
| Number of Pages: 289 pages Which Of The Following Are Secure Network Protocols Select Two |
| Publication Date: May 2020 |
| File Size: 2.3mb |
| Read Tcp Ip Protocols Working Basics Puter Work Puter Technology |
 |
The Inter Protocol Suite Article Khan Academy
| Title: The Inter Protocol Suite Article Khan Academy |
| Format: ePub Book |
| Number of Pages: 269 pages Which Of The Following Are Secure Network Protocols Select Two |
| Publication Date: October 2019 |
| File Size: 1.35mb |
| Read The Inter Protocol Suite Article Khan Academy |
 |

First What Is The Osi Model The Osi Model Is A Framework Of Protocols That Allows Two Devices To Municate On A Work Or Ov Osi Model Osi Layer Working
| Title: First What Is The Osi Model The Osi Model Is A Framework Of Protocols That Allows Two Devices To Municate On A Work Or Ov Osi Model Osi Layer Working |
| Format: ePub Book |
| Number of Pages: 276 pages Which Of The Following Are Secure Network Protocols Select Two |
| Publication Date: March 2017 |
| File Size: 1.9mb |
| Read First What Is The Osi Model The Osi Model Is A Framework Of Protocols That Allows Two Devices To Municate On A Work Or Ov Osi Model Osi Layer Working |
 |
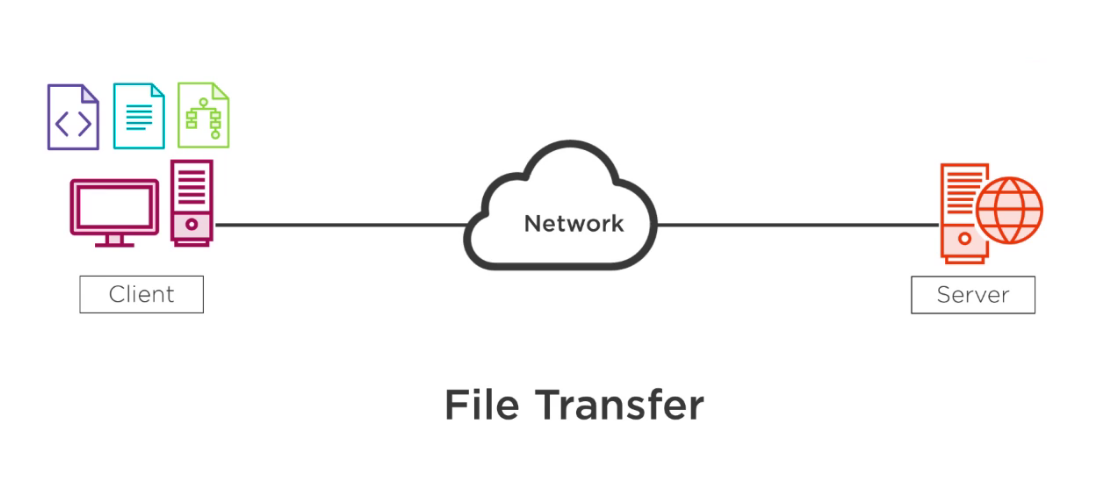
Types Of Working Protocols Top Four Major Protocols Of Working
| Title: Types Of Working Protocols Top Four Major Protocols Of Working |
| Format: PDF |
| Number of Pages: 244 pages Which Of The Following Are Secure Network Protocols Select Two |
| Publication Date: June 2019 |
| File Size: 1.6mb |
| Read Types Of Working Protocols Top Four Major Protocols Of Working |
 |
Secure Shell SSH is a cryptographic network protocol for securing data communication. This protocol uses the IDEA algorithm for encryption by default but is able to use Blowfish and DES. Answered Dec 28 2016 by Giordano_TX.
Here is all you need to read about which of the following are secure network protocols select two Below we have discussed few security protocols to protect online information. SSL and TCP B. Which of the following are the two tunneling protocols used by the majority of VPNs. 7 osi layers of munications in 2021 osi layer munication munication works puter working puter science programming working infographic puter learning 14 most mon work protocols and their vulnerabilities geeksfeeks work enterprise diagram working basics cisco working technology puter work types of working protocols top four major protocols of working types of working protocols top four major protocols of working Prioritize Those With Highest Impact First - Learn More.



No comments:
Post a Comment